Cybersecurity: the protection of internet-connected systems (ex: hardware, software, data, etc.) from cyber threats. Although a relatively recently developed field of practice, this job is extremely important because there is now an established profession that has the purpose of protecting huge tech platforms, including major social platforms (ex: instagram, facebook, snapchat, etc.) or huge voting events stored in databases. People who learn things concerning cybersecurity are able to protect various online platforms from being compromised by a foreign threat or any unauthorized access into a specific component of the database.
Cybersecurity
What is Cybersecurity? |

|
How Do Cyber-Attacks Compromise Tech Platforms?Cyber-Attacks are becoming more and more of a common problem when it comes to the technological field. For those that do not know what cyber-attacks are, they are essentially online attacks that are used to interfere and compromise with a target (a specific network). These online assaults are very wide-ranged and vary with every case; each and every conflict is very different from the other depending on what platform was attacked and to what degree the network was compromised by the cybercriminals floating through the internet. As these problems deepen further as society becomes more and more dependent on technology and computers, the development of the cybersecurity field and people who take up the profession is extremely important at this point in time. With more cybersecurity efforts, there will be more able people to stop cyber-attacks before they can become detrimental to the network and to limit the amount of online attacks made in the first place. |

|
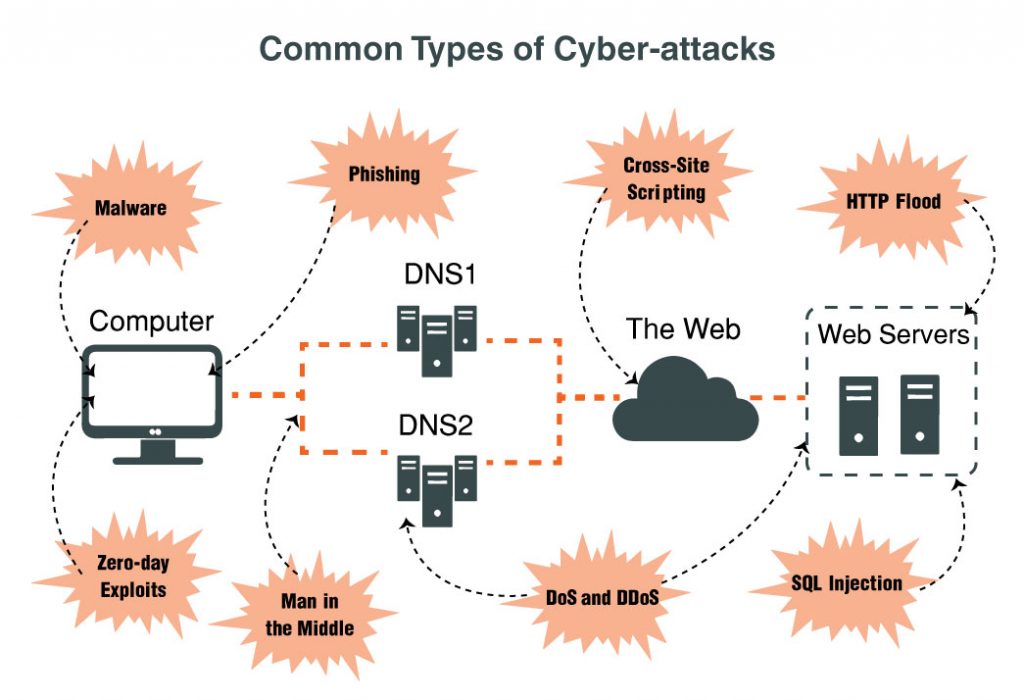
Types of Cybersecurity ThreatsThe five most common types of threats include the following: 1. Malware- a malicious software (frequently viruses) used to breach information in the targeted network 2. Phishing- social engineering attack that appears as a seemingly trusted source 3. Man-In-The-Middle Attack (MITM)- A cyber-attacker intercepts and sends messages between two parties (also known as the eavesdropping attack and often used to steal important information) 4. Distributed Denail-of-Service Attack (DDoS)- a series of attacks to the targeted central server using simultaneous data requests 5. Zero-Day Exploit: When a network vulernability is announced, there is a period of time where it remains vulnerable, allowing cyber attacks to take the opportunity to target the essentially weak network |
|